The Solar Winds Breach Case Study

We read the Solar Winds article by Temple-Raston (2021) and the description of the Cyber Kill Chain model (Hutchins et al, 2011) and carry out the following activities:.
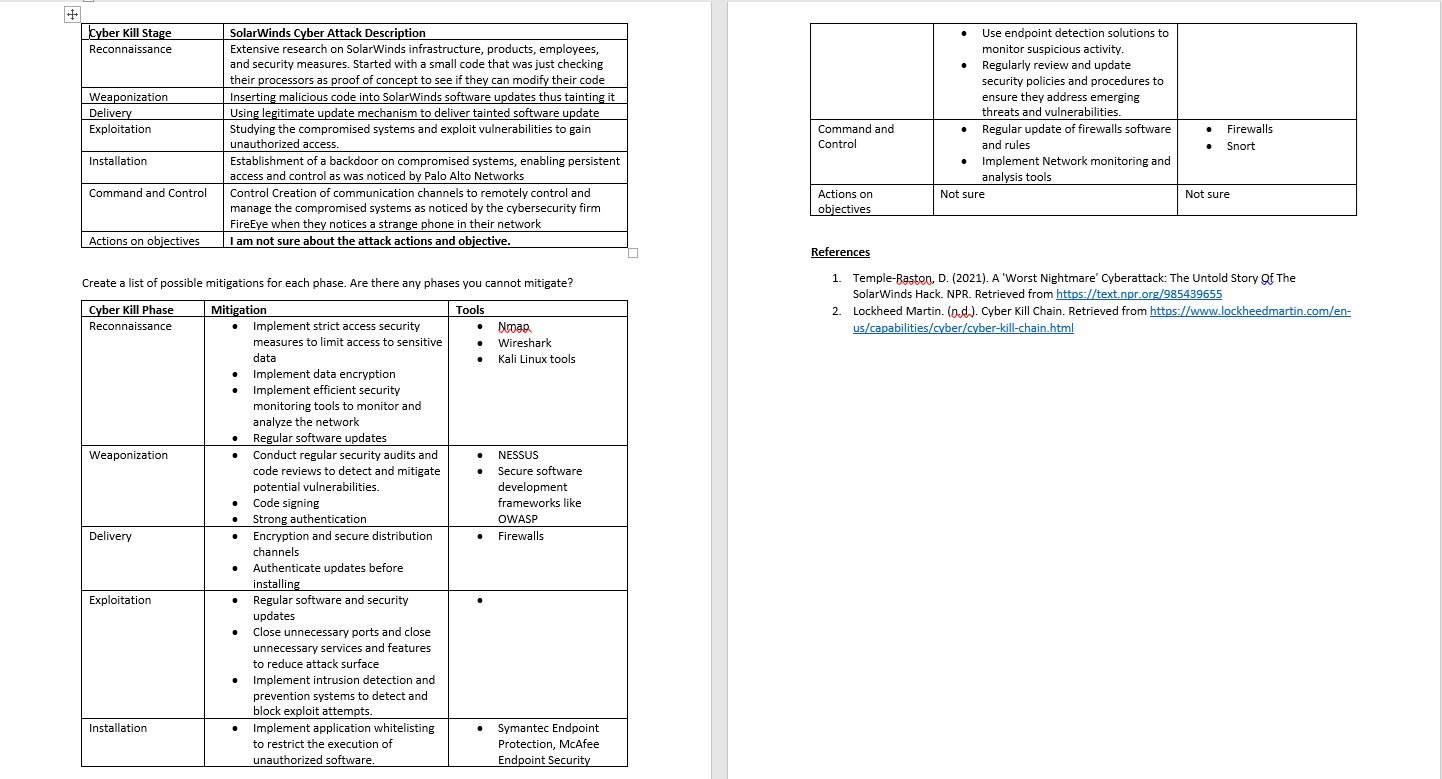
1: Create a table that analyses the solar winds exploit using the Cyber Kill Chain. Are there any phases that you cannot identify?
2. Create a list of possible mitigations for each phase. Are there any phases you cannot mitigate?
3. What tools would you utilise in each phase? Give reasons for your answer.
Below is the entire discussion that I posted in module wiki